Managed Security Awareness Training and Simulated Phishing Attacks
More than ever, employees are the weak link in an organisation’s network security. They are frequently exposed to sophisticated phishing and ransomware attacks. Employees need to be trained and remain on their toes with security top of mind.
We offer ongoing, interactive and engaging Security Awareness Training for employees supplemented with Simulated Phishing Attacks. Find out how we can help you manage the ongoing problem of social engineering and create a human firewall.

Our Partners


Why old-school Security Awareness Training doesn’t hack it anymore?
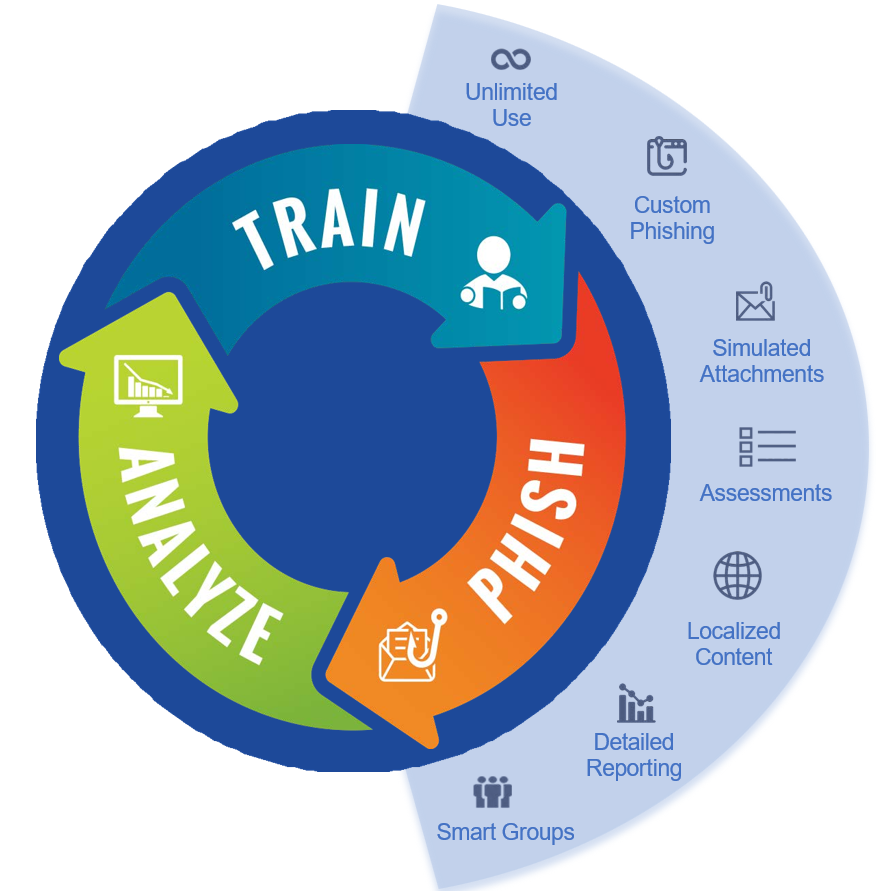
Old-school Security Awareness Training doesn’t hack it anymore. Today, your employees are frequently exposed to sophisticated phishing and ransomware attacks.
We help you keep your users on their toes with security top of mind. With our engaging and interactive service, you can train and phish your users, see their phish-prone percentage improve over time and get measurable results.
Our managed service is simple and our approach helps improve the behaviour amongst employees:
Baseline Testing
Baseline testing to assess the phish-prone percentage of your users through a simulated phishing attack.
Train Your Users
We have the world’s largest library of security awareness training content; including interactive modules, videos, games, posters and newsletters. Automated training campaigns with scheduled reminder emails.
Phish Your Users
Best-in-class, fully automated simulated phishing attacks, thousands of templates with unlimited usage, and community phishing templates.
See The Results
Enterprise-strength reporting, showing stats and graphs for both training and phishing, ready for management. Show the great ROI!
Contact us
Book a free simulated phishing test
Why Simplify Security for your security training journey?
- We work with you to develop and implement a security awareness training programme that meets your needs and fit your culture. We then manage this for you.
- We do this for a living and are constantly adopting new techniques that fit your organisation culture.
- Our security training is engaging, interactive and frequent.
- We have content in multiple languages.
- We have enterprise-grade reporting to track improvement and demonstrate ROI.
- We help you put together all processes to deal with phishing attacks – we work with most NZ IT providers.
- We help train your users with simulated phishing attacks and allow them to report phishing emails safely.
- We have personality! Security training doesn’t have to be dull.


Did you know that 91% of successful data breaches started with a spear-phishing attack?
Find out what percentage of your employees are phish-prone with your free phishing security test. Plus, see how you stack up against your peers with the new phishing Industry Benchmarks!
IT pros and business owners have realised that simulated phishing tests are urgently needed as an additional security layer. Today, phishing your own users is just as important as having antivirus and multi-factor authentication. It is a fun and effective cybersecurity best practice to patch your last line of defence: USERS
Why? If you don’t do it yourself, the bad guys will.
Here’s how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Select from 20+ languages and customize the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a report emailed to you in 24 hours with your phish-prone % and charts to share with management
- See how your organisation compares to others in your industry
Security training doesn’t need to be boring. Talk to us today!
Book a free simulated phishing test
Why Simplify Security?

Reliability you can trust
Let’s face it, Kiwis can be a bit laid back and that sometimes means companies not returning your calls, turning up on time or delivering on promises. Not us – we pride ourselves on reliability, dependability and integrity.

Skilled staff
We all know there is a skills shortage in cyber security. Forget the stress of recruitment and retention by leveraging our highly skilled professionals. Just look at their accreditations - they know their stuff.

Cost-effective services
Employing a full time cyber security professional is not an affordable option for most SMBs. We offer competitive, affordablele and flexible subscriptions with no long term restrictive contracts.

Leading protection
Artificial Intelligence (AI) and automation are at our core. We use the power of AI to predict and protect against known and unknown threats, to keep your business and interests safe.
Case Study
This customer reached out to our cyber security consultants when they suffered a considerable financial loss after falling victim to a spear-phishing attack.
The attacker was able to gain access to the email platform and monitor the email flow and exfiltrate contacts of our customer. The attacker had been lurking in their Office 365 for months, reading emails and learning about their processes and partners. Once they had gained the required knowledge, they launched their simple but effective attack. Posing as one of our customer’s partners, they sent a spoof email requesting their bank account details to be changed and for funds to be transferred into the new account. The email was sent to the correct employee and was a good imitation of how the partner’s emails usually look. Acting as instructed, the employee changed the account details and transferred the funds.

Frequently Asked Questions
See our cybersecurity risk assessment frequently asked questions below for help and advice.
What is the NIST cyber security framework?
The NIST Cyber security Framework was first published in 2014 following an Executive Order directing NIST to develop a voluntary framework for reducing cyber risk. The Framework is based on existing standards and guidelines. It organizes cyber security controls into five concurrent and continuous functions—Identify, Protect, Detect, Respond, and Recover. When considered together, these functions provide a high-level, strategic view of the lifecycle of an organization’s management of cybersecurity risk.
The Framework has since been widely adopted by organizations of all sizes as a tool to help manage cyber security risk. Achieving and maintaining an adequate standard of cyber security in a business is a complex endeavor. The adoption of a well-recognized framework, such as NIST, is essential to success. Our IT Security Risk Assessments are fully compliant to the scheme.
Is a cyber security risk assessment the same as a cyber security audit?
Not exactly but they are related. A cyber security audit focusses on giving you an overall picture of your cyber security posture and where your gaps are. This is sometimes also referred to as a cyber security health check. Our IT risk assessments go further than this by advising of the risk as it relates to your unique business position by identifying the threats your business is exposed to, assessing your vulnerabilities and identifying the critical assets you need to protect. We then advise of security controls you can put in place to mitigate these risks.
Blog
The Dark Reality: Unveiling the Human Factor Driving the Surge in Cyber Breaches
Human error continues to be one of the leading causes of cyber breaches, posing significant threats to businesses and individuals alike. In fact, according to a report by IBM, 95% of all cybersecurity incidents involve human error, with the average cost of a data...
Your Ultimate Guide to Understanding NIST Cyber Security Framework 2.0 Update
As threats in the digital realm evolve, the NIST Cyber security framework (CSF) 2.0 serves as a crucial resource to help businesses of all sizes, across industries to reinforce their defences against cyber security threats. This updated guidance focuses on a...
Key Takeaways from the CrowdStrike 2024 Global Threats Report
CrowdStrike’s new 2024 Global Threat Report has been creating some buzz around the latest trends in the cyberattacks, and we are here to make the key takeaways from the main topics that were talked about in the report more accessible to you. To summarise, the...







